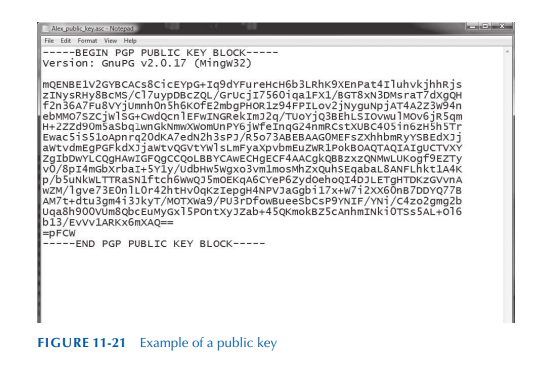
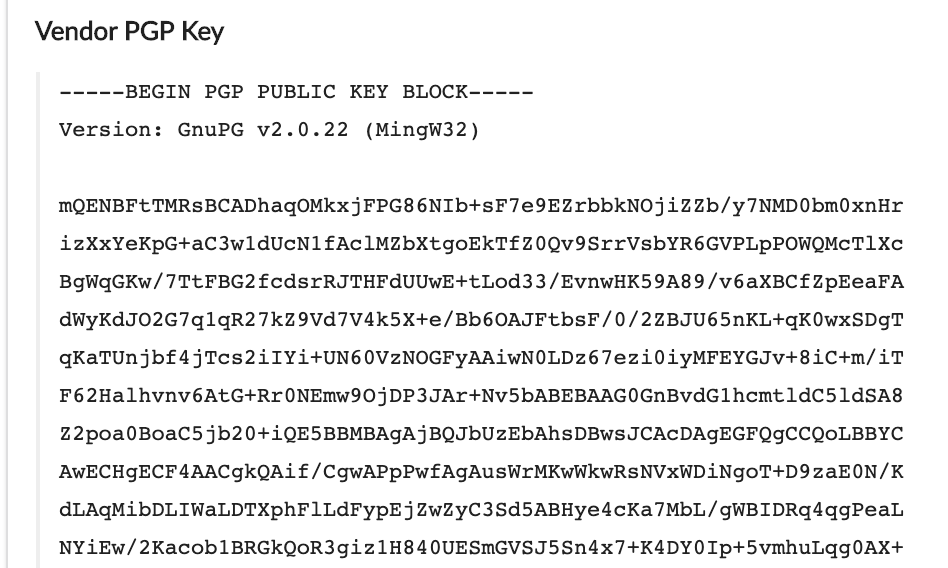
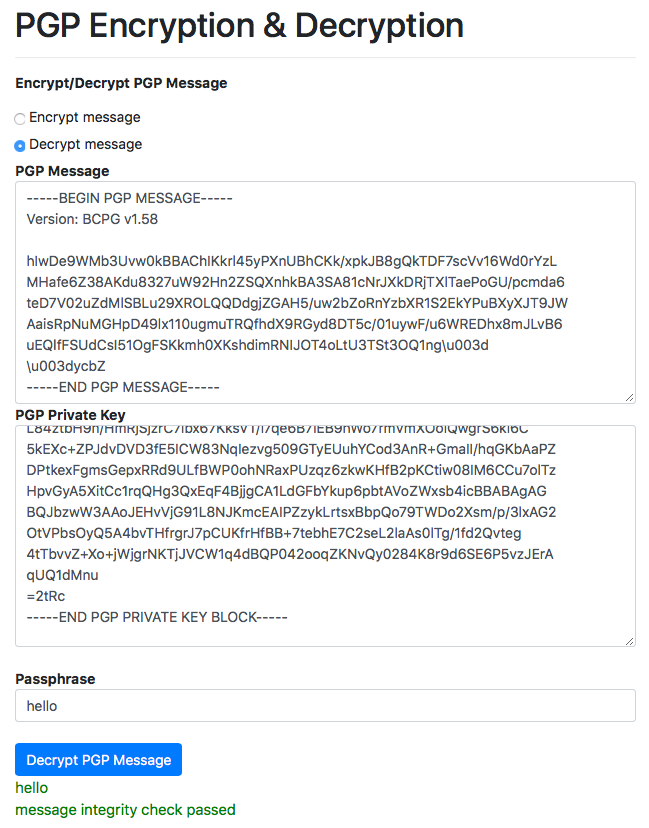
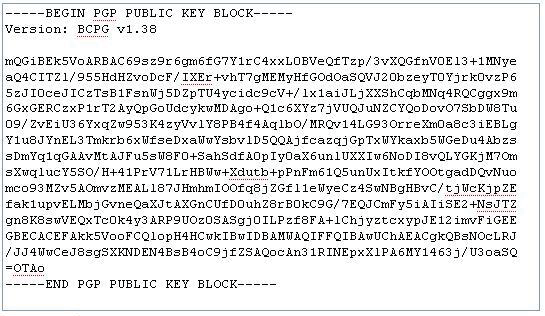
openpgp - How to tell if a "PGP PRIVATE KEY BLOCK" is passphrase protected? - Information Security Stack Exchange
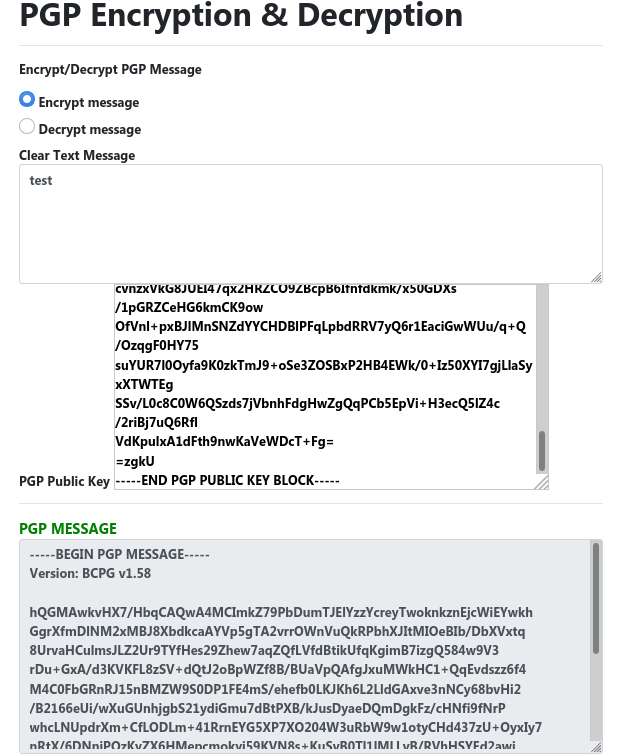
How To Make a PGP Keypair using GPG and Communicate In Absolute Privacy (Linux/Mac) Public & Private Keys + Encrypt & Decrypt Messages - Sick Codes - Security Research, Hardware & Software
Article: Implementing AES Symmetric Enryption with a PGP Public Key Certificate and the Custom Scripting Component - Boomi Community

Step by step procedure Generate PGP keys and End to end iflow to encrypt-and-decrypt with Signatures | SAP Blogs

pgp - Why is GnuPG changing first two characters of ascii armored public key after downloading it from the key server? - Cryptography Stack Exchange
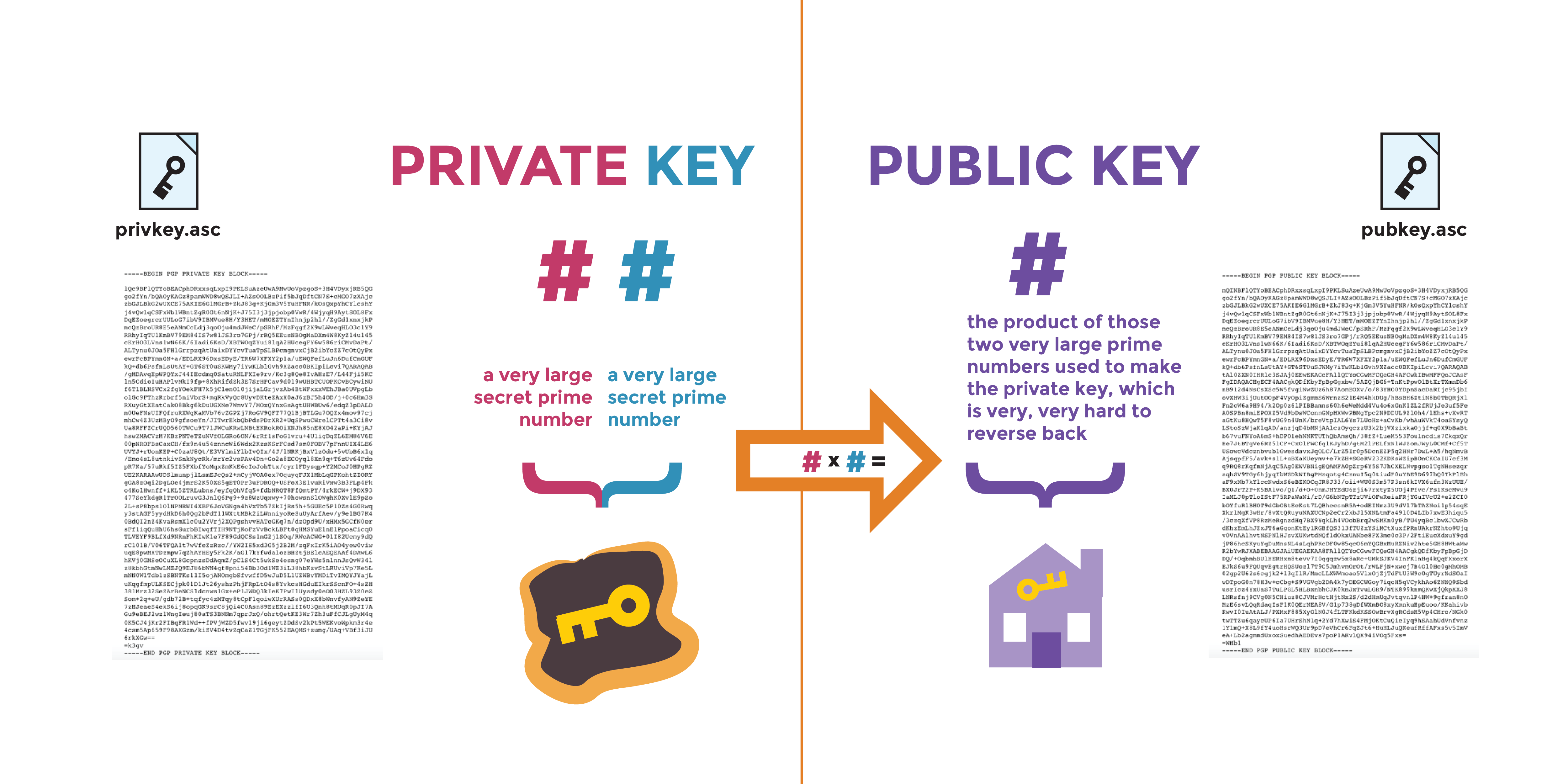

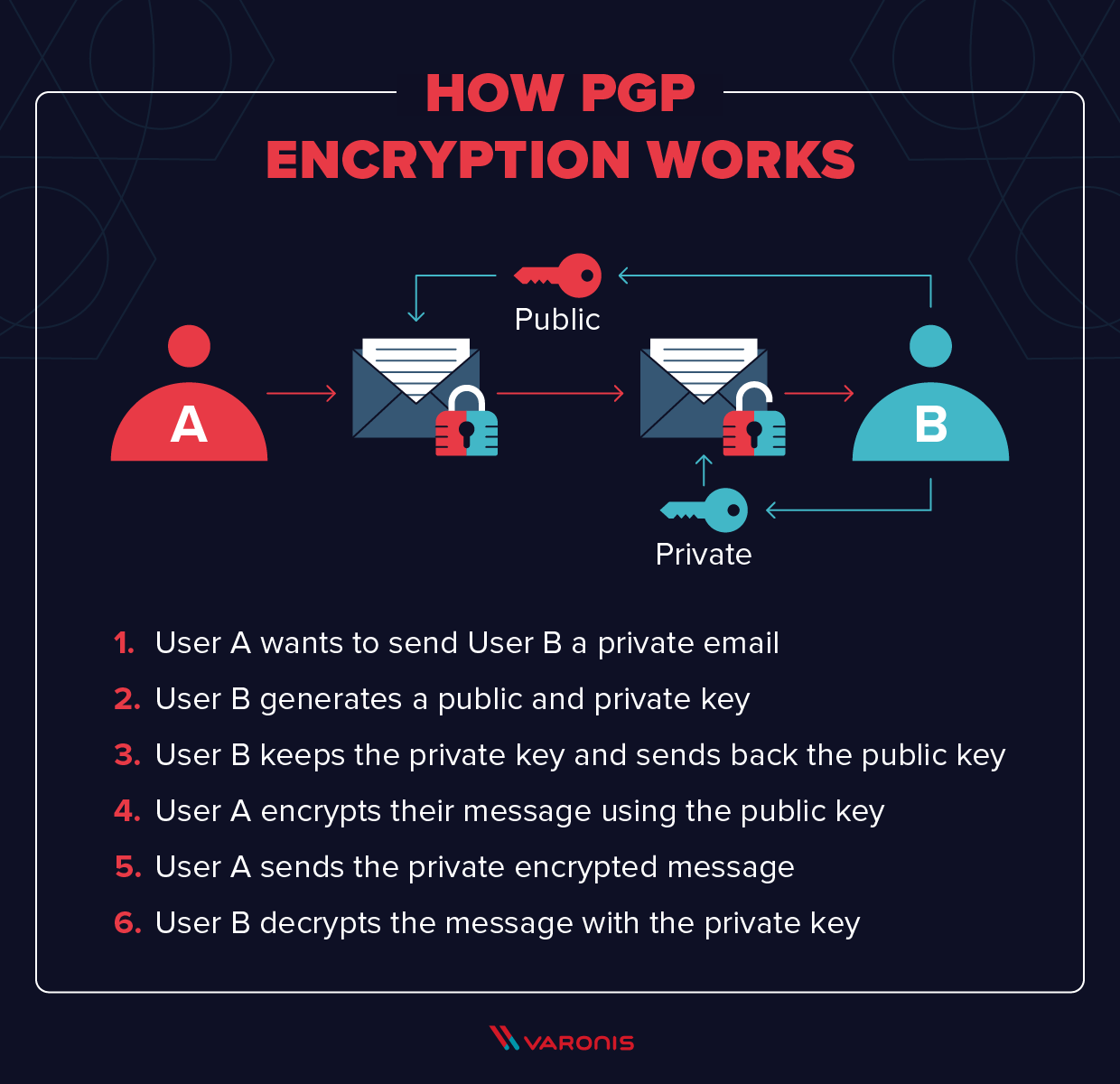

![Tutorial] How do PGP keys work - Jacob Riggs | Blog Tutorial] How do PGP keys work - Jacob Riggs | Blog](https://jacobriggs.io/blog/app/web/upload/misc/pgp-encryption-diagram.png)